QuickLogic Corporation has announced that it has partnered with Intrinsic ID to provide security options for devices incorporating embedded FPGA (eFPGA) technology. These options range from secure key generation based on SRAM PUF to full security solutions including bitstream encryption, key wrapping, authentication tags, key verification, and data encryption/decryption for storage within the device or for board or system-level communications. This partnership has created a seamless integration of the solutions of both companies, allowing QuickLogic’s eFPGA customers to add security functionality without any further integration effort.
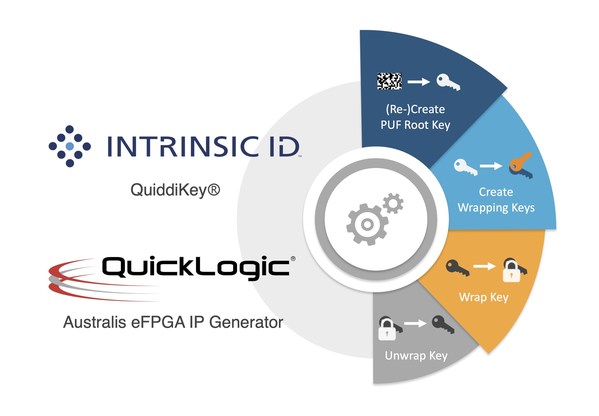
Intrinsic ID’s solutions are based on Physical Unclonable Functions, or PUFs, which are unique physical characteristic of a specific device that can be used to generate a device-specific encryption key. For SoCs using eFPGA technology, the PUF can be standard SRAM cells or FPGA logic cells specifically configured for PUF purposes. In either case, the PUF gives each individual device a unique digital fingerprint, which can be used to generate an encryption root key whenever it is needed. This approach avoids the need to store the key and thus expose it to hackers. It also ensures that each key is unique to the specific device in which it is generated.
In addition to PUF-based key generation, Intrinsic ID offers a complete SoC security solution called QuiddiKey, which adds functionality including encrypting secret keys and data, deriving wrapping keys to protect other functions, adding authentication tags, and verifying authentication tags and decrypting the associated contents. The benefits of this approach include offering a higher level of security than traditional key storage, enabling the creation and storage of an unlimited number of secure keys, and minimizing hardware overhead. QuiddiKey also enables the wrapping of keys used for bitstream encryption with device unique keys, allowing device owners to protect the device and valuable IP so a trusted supply chain is guaranteed.